Security Cloud Data With VPS Servers Deal – Secure Cloud Data with VPS Servers: A Deal You Can’t Refuse sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. Imagine a world where your precious data is safe and sound, protected by a fortress of digital security.
This is the promise of VPS servers, offering a level of control and customization that traditional shared hosting environments simply can’t match.
VPS servers, or Virtual Private Servers, provide a dedicated slice of a physical server’s resources, giving you a virtual machine that acts like its own independent computer. This means your data is isolated from other users, making it significantly harder for hackers to gain access.
Think of it as having your own private apartment in a massive skyscraper, complete with its own security system and access controls.
VPS Servers
In the realm of cloud data security, VPS servers emerge as a robust foundation, offering a compelling alternative to shared hosting environments. VPS servers, or Virtual Private Servers, provide a dedicated slice of a physical server’s resources, offering a unique blend of control, isolation, and customization, which are crucial for safeguarding sensitive data.
Advantages of VPS Servers for Data Security
VPS servers offer a distinct advantage over shared hosting environments by providing a dedicated and isolated environment for your data. This isolation prevents other users on the same physical server from accessing or compromising your data.
- Enhanced Control:VPS servers empower you with root access, granting complete control over the server’s operating system, software, and configurations. This allows you to implement stringent security measures, customize firewalls, and monitor system activity for potential threats.
- Improved Security Posture:The ability to customize your VPS server environment allows you to install and configure security software, such as antivirus, intrusion detection systems, and firewalls, tailored to your specific security needs.
- Reduced Risk of Data Breaches:In a shared hosting environment, a security breach on one account can potentially compromise the entire server, including your data. VPS servers provide an isolated environment, minimizing the risk of data breaches caused by other users’ vulnerabilities.
Examples of VPS Server Security Enhancements
Consider a scenario where a website hosted on a shared hosting environment experiences a malware infection. The malware can potentially spread to other websites on the same server, compromising their data and security. In contrast, a website hosted on a VPS server is isolated from other websites, preventing the spread of malware and protecting sensitive data.Another example involves a website hosted on a shared hosting environment that experiences a denial-of-service (DoS) attack.
The attack can overload the server’s resources, making it unavailable for all users, including your website. A VPS server, with its dedicated resources, can better withstand such attacks, ensuring the availability and security of your data.
Security Measures for Cloud Data on VPS Servers
Securing cloud data on VPS servers is crucial for protecting sensitive information from unauthorized access, breaches, and data loss. VPS servers offer flexibility and control over resources, but they also come with the responsibility of implementing robust security measures. By adopting a comprehensive approach to security, you can mitigate risks and safeguard your cloud data effectively.
Firewalls and Intrusion Detection Systems
Firewalls are essential for protecting VPS servers from unauthorized access. They act as a barrier between your server and the outside world, filtering incoming and outgoing network traffic based on predefined rules. Firewalls can block malicious traffic, prevent unauthorized access, and help protect against common vulnerabilities.
- Hardware firewalls: These are physical devices that are dedicated to filtering network traffic. They offer high performance and advanced security features.
- Software firewalls: These are applications that run on your server and provide similar functionality to hardware firewalls. They are more affordable and easier to implement.
Intrusion detection systems (IDS) are software tools that monitor network traffic for suspicious activity. They can detect potential threats, such as malware, unauthorized access attempts, and denial-of-service attacks. IDS can alert administrators to potential threats, allowing them to take timely action to mitigate risks.
- Signature-based IDS: These systems rely on a database of known attack patterns to detect threats. They are effective against known attacks, but they may not be able to detect new or unknown threats.
- Anomaly-based IDS: These systems analyze network traffic for deviations from normal patterns.They can detect new and unknown threats, but they may generate false positives.
Data Backup and Disaster Recovery Strategies

Data backup and disaster recovery plans are essential for safeguarding your cloud data on VPS servers. They ensure data integrity and availability, allowing you to recover from data loss or system failures. A comprehensive strategy includes regular backups, robust recovery procedures, and a well-defined plan for business continuity.
Backup Methods for VPS Servers
Different backup methods are available, each with its advantages and disadvantages. Choosing the right method depends on factors like data volume, recovery time objectives (RTO), and recovery point objectives (RPO).
- Full Backups: This method creates a complete copy of all data on the VPS server. Full backups are ideal for initial backups or when you need to restore all data. However, they can take a significant amount of time and storage space.Enhance your insight with the methods and methods of Benefits of AWS Cloud Computing for Small Businesses.
- Incremental Backups: Incremental backups only capture changes made since the last full or incremental backup. They are faster and more efficient than full backups but require a full backup to restore data.
- Differential Backups: Differential backups capture all changes made since the last full backup. They are faster than full backups but require a full backup and the last differential backup for restoration.
- Cloud-Based Backups: Cloud-based backup services offer off-site data storage and automated backup schedules. They provide scalability, security, and disaster recovery capabilities.
Disaster Recovery Plan
A comprehensive disaster recovery plan Artikels procedures for data restoration and business continuity in the event of a disaster. The plan should include the following elements:
- Data Recovery Procedures: Detailed steps for restoring data from backups, including the specific backup method, recovery tools, and recovery time objectives.
- Business Continuity Plan: Strategies for maintaining critical business operations during a disaster, such as alternative work arrangements, communication protocols, and customer support procedures.
- Testing and Evaluation: Regular testing of the disaster recovery plan to ensure its effectiveness and identify areas for improvement.
Compliance and Regulatory Considerations
Storing data on VPS servers involves navigating a complex landscape of regulations and compliance standards designed to protect sensitive information. Understanding and adhering to these requirements is crucial for maintaining data integrity, preventing breaches, and upholding legal obligations.
Data Security Regulations and Compliance Standards
Data security regulations and compliance standards are designed to ensure that organizations take appropriate measures to protect sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. These standards vary depending on the industry, location, and type of data being handled.
Some of the most prominent regulations and standards include:
- General Data Protection Regulation (GDPR):This EU regulation applies to any organization that processes personal data of individuals residing in the EU, regardless of the organization’s location. It mandates stringent data protection principles, including data minimization, transparency, and individual rights.
- California Consumer Privacy Act (CCPA):This California law grants consumers specific rights over their personal data, including the right to know what data is collected, the right to delete data, and the right to opt out of data sales.
- Health Insurance Portability and Accountability Act (HIPAA):This US law governs the protection of protected health information (PHI) in the healthcare industry. It requires organizations to implement robust security measures to safeguard patient data.
- Payment Card Industry Data Security Standard (PCI DSS):This standard applies to organizations that process, store, or transmit credit card information. It Artikels specific security requirements for protecting cardholder data, including encryption, access control, and vulnerability management.
- ISO 27001:This international standard provides a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). It covers a wide range of security controls, including risk management, access control, and incident response.
Configuring VPS Servers for Compliance
VPS servers can be configured to meet compliance requirements through various security measures. These include:
- Access Control:Implement strong authentication mechanisms, such as multi-factor authentication (MFA), to restrict unauthorized access to VPS servers.
- Data Encryption:Encrypt data at rest and in transit to protect it from unauthorized access. Utilize strong encryption algorithms and regularly update encryption keys.
- Regular Security Audits:Conduct periodic security audits to identify vulnerabilities and ensure compliance with regulations.
- Security Monitoring and Logging:Monitor VPS server activity for suspicious behavior and maintain detailed logs of all actions taken.
- Vulnerability Management:Regularly scan for and patch vulnerabilities to prevent attackers from exploiting weaknesses in the server’s software and operating system.
Industry Best Practices for Data Security and Compliance
Industry best practices provide a roadmap for implementing robust data security measures and maintaining compliance with relevant regulations. These practices include:
- Data Minimization:Only collect and store data that is absolutely necessary for business operations.
- Data Retention Policies:Establish clear data retention policies to determine how long data should be stored and when it should be deleted.
- Data Security Training:Train employees on data security best practices and their responsibilities under relevant regulations.
- Incident Response Plan:Develop a comprehensive incident response plan to handle data breaches and other security incidents effectively.
- Third-Party Risk Management:Conduct due diligence on third-party vendors and service providers to ensure they have adequate security measures in place.
Best Practices for Securing Cloud Data with VPS Servers
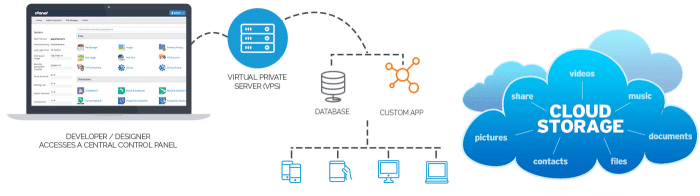
Securing your cloud data on VPS servers is crucial for protecting sensitive information from unauthorized access, data breaches, and other cyber threats. Implementing robust security practices is essential to ensure the confidentiality, integrity, and availability of your data.
Strong Passwords and User Access Controls, Security Cloud Data With VPS Servers Deal
Strong passwords are the first line of defense against unauthorized access to your VPS server. It is vital to use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable passwords like your name, birthdate, or common phrases.
- Use a password manager:Password managers can help you generate and store strong, unique passwords for each of your accounts, making it easier to manage your security.
- Enable two-factor authentication (2FA):2FA adds an extra layer of security by requiring you to enter a code sent to your phone or email in addition to your password when logging in.
- Implement role-based access control (RBAC):RBAC assigns specific permissions to users based on their roles within your organization, ensuring that only authorized individuals have access to sensitive data.
- Regularly audit user accounts:Regularly review user accounts to ensure that only active users have access to your VPS server and that their permissions are appropriate.
Data Encryption
Data encryption is a crucial security measure that transforms data into an unreadable format, making it inaccessible to unauthorized individuals. Encrypting your data both in transit and at rest helps protect it from potential threats.
- Use Transport Layer Security (TLS):TLS encrypts data transmitted between your VPS server and clients, protecting it from eavesdropping and data interception.
- Encrypt data at rest:Encrypt sensitive data stored on your VPS server using strong encryption algorithms like Advanced Encryption Standard (AES).
- Use encryption tools:Consider using encryption tools like VeraCrypt or BitLocker to encrypt your entire hard drive or specific files.
Security Settings and Monitoring
Configuring appropriate security settings and monitoring your VPS server for potential threats is essential for proactive security.
- Keep your software up to date:Regularly update your operating system, applications, and security software to patch vulnerabilities and protect your server from known exploits.
- Enable firewalls:Firewalls act as a barrier between your VPS server and the outside world, blocking unauthorized access and malicious traffic.
- Implement intrusion detection and prevention systems (IDS/IPS):IDS/IPS systems monitor network traffic for suspicious activity and can block or alert you to potential threats.
- Regularly monitor system logs:Review system logs for any unusual activity or error messages that may indicate a security breach.
Security Best Practices
- Regularly back up your data:Data backups provide a safety net in case of data loss due to accidental deletion, hardware failure, or a security breach.
- Use strong and unique passwords for all accounts:Use a combination of uppercase and lowercase letters, numbers, and special characters to create strong passwords. Avoid using the same password for multiple accounts.
- Implement multi-factor authentication (MFA):MFA adds an extra layer of security by requiring you to enter a code sent to your phone or email in addition to your password when logging in.
- Keep your software up to date:Regularly update your operating system, applications, and security software to patch vulnerabilities and protect your server from known exploits.
- Enable firewalls:Firewalls act as a barrier between your VPS server and the outside world, blocking unauthorized access and malicious traffic.
- Implement intrusion detection and prevention systems (IDS/IPS):IDS/IPS systems monitor network traffic for suspicious activity and can block or alert you to potential threats.
- Regularly monitor system logs:Review system logs for any unusual activity or error messages that may indicate a security breach.
- Limit access to sensitive data:Only grant access to sensitive data to authorized individuals who need it to perform their job duties.
- Educate your users about security best practices:Train your users on how to identify and avoid phishing scams, malware, and other security threats.
- Regularly review your security policies and procedures:Ensure that your security policies and procedures are up-to-date and effective in protecting your data.
Real-World Examples and Case Studies: Security Cloud Data With VPS Servers Deal

In the realm of cloud data security, real-world examples provide valuable insights into the effectiveness of various security measures and how VPS servers have been instrumental in safeguarding sensitive information. These case studies showcase how different organizations have tackled unique security challenges and implemented solutions tailored to their specific needs.
Case Studies of VPS Server Use for Cloud Data Security
Understanding the effectiveness of various security measures in different scenarios is crucial for informed decision-making. Let’s delve into some real-world examples that demonstrate how VPS servers have been utilized to secure sensitive cloud data:
Financial Services
- Use Case:A leading financial institution adopted VPS servers to host its online banking platform, ensuring secure access to customer accounts and financial transactions.
- Security Challenges:The platform faced threats from malicious actors seeking to compromise customer data and financial information.
- Solutions Implemented:The institution implemented a multi-layered security approach, including:
- Robust firewalls to prevent unauthorized access.
- Intrusion detection systems (IDS) to monitor network traffic for suspicious activity.
- Regular security audits to identify and mitigate vulnerabilities.
- Data encryption to protect sensitive information at rest and in transit.
- Effectiveness:The security measures implemented on the VPS servers effectively mitigated security risks, protecting customer data and ensuring the integrity of financial transactions.
Healthcare
- Use Case:A healthcare provider leveraged VPS servers to host its electronic health records (EHR) system, ensuring secure storage and access to patient data.
- Security Challenges:The healthcare industry faces strict regulations regarding data privacy and security, making it imperative to protect sensitive patient information.
- Solutions Implemented:The provider implemented a comprehensive security strategy, including:
- Secure access controls to restrict unauthorized access to patient data.
- Data encryption to protect patient information at rest and in transit.
- Regular security updates and patches to address vulnerabilities.
- Compliance with industry standards such as HIPAA and GDPR.
- Effectiveness:The security measures implemented on the VPS servers ensured the confidentiality, integrity, and availability of patient data, meeting regulatory requirements and safeguarding patient privacy.
E-commerce
- Use Case:An e-commerce company used VPS servers to host its online store, providing secure payment processing and customer data management.
- Security Challenges:E-commerce platforms are susceptible to attacks such as data breaches, payment fraud, and denial-of-service attacks.
- Solutions Implemented:The company implemented a multi-layered security approach, including:
- Secure socket layer (SSL) encryption to protect sensitive data during transactions.
- Two-factor authentication for user logins.
- Fraud detection systems to prevent fraudulent transactions.
- Regular security assessments to identify and address vulnerabilities.
- Effectiveness:The security measures implemented on the VPS servers effectively mitigated security risks, protecting customer data, preventing fraud, and ensuring the reliability of the e-commerce platform.
Conclusion
Securing your cloud data with VPS servers is an investment in peace of mind. By implementing robust security measures, utilizing data backup and disaster recovery strategies, and staying compliant with industry regulations, you can create a digital fortress that protects your most valuable assets.
So, embrace the power of VPS servers and unlock a world where your data is safe, secure, and always accessible, no matter what challenges lie ahead.
FAQ
What are the most common security threats to cloud data?
Common threats include data breaches, malware attacks, denial-of-service attacks, and unauthorized access.
How can I choose the right VPS server for my needs?
Consider factors like storage space, RAM, processing power, and the location of the server. Research different providers and compare their offerings and pricing.
Are there any free VPS server options available?
While free VPS servers exist, they often come with limited resources and may not be suitable for critical data storage. Consider your specific needs and budget before choosing a free option.