The Ultimate Guide to API Security for IoT delves into the critical realm of securing the vast network of interconnected devices that are transforming our world. As the Internet of Things (IoT) continues to proliferate, so too does the vulnerability of these devices to malicious actors.
The interconnected nature of the IoT landscape creates a unique set of challenges for security professionals, requiring a comprehensive understanding of API security best practices to protect sensitive data and ensure the integrity of these critical systems.
This guide provides a roadmap for navigating the complexities of API security in the IoT context. It explores the fundamental security principles that underpin secure API design, development, and deployment, while also addressing the ever-evolving landscape of threats targeting IoT devices.
From secure authentication and authorization to data encryption and vulnerability management, this guide equips readers with the knowledge and tools needed to build a robust and resilient API security framework.
Introduction to API Security in the IoT Landscape
The Internet of Things (IoT) is rapidly evolving, connecting billions of devices to the internet. This interconnectedness brings immense benefits, but it also introduces significant security risks. APIs, acting as the communication bridge between devices and applications, play a crucial role in this ecosystem.
As the number of connected devices and the complexity of IoT systems grow, the importance of API security becomes paramount.APIs in IoT environments face unique challenges and vulnerabilities that require specific security measures.
API Security Challenges in IoT
The interconnected nature of IoT systems presents unique challenges for API security. Here are some of the key vulnerabilities:
- Limited Device Resources:Many IoT devices have limited processing power, memory, and battery life, making it challenging to implement robust security measures.
- Diverse Device Types:IoT ecosystems encompass a wide range of devices with varying operating systems, protocols, and security capabilities, making it difficult to enforce consistent security standards across the entire ecosystem.
- Open Communication Channels:IoT devices often communicate over public networks, making them vulnerable to eavesdropping and man-in-the-middle attacks.
- Lack of Security Awareness:Many IoT device manufacturers and developers lack adequate security awareness and expertise, leading to insecure API designs and implementations.
Real-World Examples of API Security Breaches in IoT, The Ultimate Guide to API Security for IoT
Several high-profile API security breaches have occurred in the IoT sector, highlighting the importance of robust security measures.
- Mirai Botnet:The Mirai botnet, which launched massive distributed denial-of-service (DDoS) attacks, exploited vulnerabilities in IoT devices, including weak default passwords and insecure APIs.
- Kaspersky’s Smart Home Security Breach:In 2019, a security researcher discovered vulnerabilities in Kaspersky’s smart home security system, allowing attackers to gain control of devices through insecure APIs.
- IoT Device Hijacking:In 2020, researchers demonstrated the ability to hijack IoT devices, such as smart TVs and routers, by exploiting vulnerabilities in their APIs.
Fundamental Security Principles for IoT APIs
Securing IoT APIs is paramount for ensuring the safety and reliability of connected devices. This section delves into the fundamental security principles that form the bedrock of secure API design, development, and deployment in the IoT landscape.
Secure API Design Principles
Secure API design is a proactive approach to mitigating vulnerabilities. It involves incorporating security considerations into the API’s architecture and implementation from the outset.
- Least Privilege Principle:APIs should be designed to operate with the minimum privileges necessary to perform their intended functions. This principle helps to limit the potential impact of security breaches, as compromised APIs will have restricted access to sensitive data and resources.
- Input Validation and Sanitization:Rigorous input validation and sanitization are crucial for preventing injection attacks, such as SQL injection and cross-site scripting (XSS). APIs should validate and sanitize all input data, ensuring that it conforms to expected formats and does not contain malicious code.
- Secure Communication:All communication between IoT devices and APIs should be encrypted using robust protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL). Encryption ensures that data transmitted over the network is protected from eavesdropping and tampering.
- Rate Limiting:Implementing rate limiting mechanisms helps to prevent denial-of-service (DoS) attacks by limiting the number of requests an API can receive within a specific timeframe. This prevents malicious actors from overloading the API with excessive requests, disrupting its functionality.
- Secure Logging and Monitoring:Comprehensive logging and monitoring of API activity are essential for detecting and responding to security incidents. Logs should capture details about API calls, user actions, and system events, enabling security teams to identify suspicious patterns and potential threats.
Authentication and Authorization
Authentication and authorization are fundamental security mechanisms for verifying the identity of users and controlling their access to resources.
- Authentication:This process confirms the identity of a user or device attempting to access the API. Strong authentication mechanisms, such as multi-factor authentication (MFA) or digital certificates, are crucial for preventing unauthorized access.
- Authorization:Once authenticated, authorization determines the level of access a user or device has to specific API resources. This is achieved through access control lists (ACLs) or role-based access control (RBAC), which define permissions for different users and roles.
Encryption for Data Protection
Encryption is a critical security measure that protects sensitive data both at rest and in transit.
- Data at Rest Encryption:This involves encrypting data stored on servers or databases. Strong encryption algorithms, such as Advanced Encryption Standard (AES), should be used to safeguard data from unauthorized access.
- Data in Transit Encryption:As discussed earlier, secure communication protocols like TLS/SSL encrypt data during transmission between IoT devices and APIs. This prevents eavesdropping and data tampering while data is being transferred over the network.
Secure API Development Practices
Secure development practices play a vital role in minimizing vulnerabilities and ensuring the overall security of IoT APIs.
- Secure Coding Practices:Developers should adhere to secure coding standards and best practices to prevent common vulnerabilities such as buffer overflows, cross-site scripting (XSS), and SQL injection.
- Regular Security Audits:Conducting regular security audits and penetration testing helps identify and address potential vulnerabilities in the API codebase. These audits should be performed by independent security experts to ensure objectivity and thoroughness.
- Code Review and Static Analysis:Code review and static analysis tools can help identify security flaws early in the development cycle. These tools analyze the source code for potential vulnerabilities and provide recommendations for remediation.
- Secure Deployment Practices:Secure deployment practices are crucial for protecting the API from attacks during the deployment process. This includes using secure deployment tools and configurations, as well as ensuring that the API is deployed in a secure environment.
Common API Security Threats in IoT
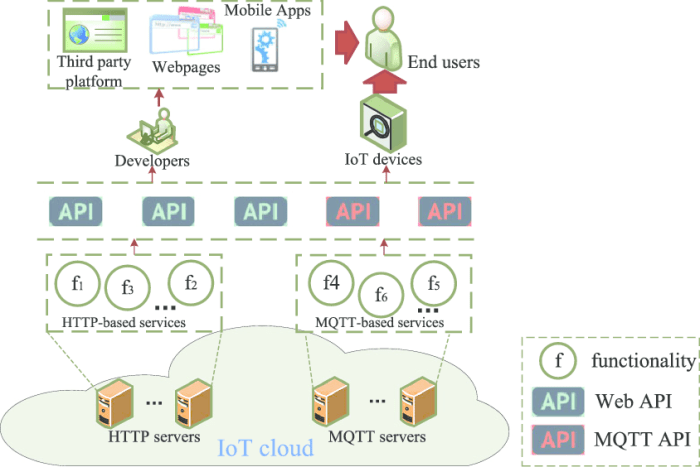
The interconnected nature of IoT devices and systems makes them particularly vulnerable to various API security threats. These threats can exploit vulnerabilities in the communication protocols, authentication mechanisms, and data handling practices of IoT APIs, potentially compromising the confidentiality, integrity, and availability of sensitive data and critical functionalities.
Unauthorized Access
Unauthorized access to IoT APIs can lead to the compromise of sensitive data, control over devices, and disruption of services. Attackers can exploit weak authentication mechanisms, default credentials, or vulnerabilities in API authorization protocols to gain unauthorized access.
- Credential Stuffing:Attackers can use stolen or leaked credentials from other breaches to attempt to log in to IoT APIs. This method is particularly effective when devices use default or easily guessable credentials.
- Brute Force Attacks:Attackers can try to guess passwords or API keys by repeatedly submitting different combinations until they find the correct one.
- API Key Exposure:If API keys are stored insecurely or exposed in the client-side code, attackers can intercept them and use them to access the API without authorization.
Data Manipulation
Attackers can manipulate data transmitted through IoT APIs to gain unauthorized access, alter device settings, or disrupt normal operations. Data manipulation attacks can involve modifying data payloads, injecting malicious code, or altering the intended functionality of the API.
- Data Injection:Attackers can inject malicious data into API requests or responses, potentially altering device settings, manipulating sensor readings, or causing unexpected behavior.
- Data Modification:Attackers can modify data transmitted through the API, such as sensor readings or device commands, to manipulate the behavior of the device or system.
- Data Poisoning:Attackers can introduce false or misleading data into the API, potentially corrupting the system’s data integrity or leading to incorrect decisions.
Denial-of-Service Attacks
Denial-of-service (DoS) attacks aim to disrupt the availability of IoT APIs by overloading the server or network infrastructure with excessive requests. This can prevent legitimate users from accessing the API and disrupt critical services.
- Resource Exhaustion:Attackers can flood the API server with requests, consuming its resources and making it unavailable to legitimate users.
- API Flooding:Attackers can send a large number of requests to the API, overwhelming its processing capacity and causing it to become unresponsive.
- Slowloris Attacks:Attackers can send requests that take a long time to process, consuming the server’s resources and making it slow to respond to legitimate users.
Secure API Development Practices for IoT
Developing secure APIs for the Internet of Things (IoT) is paramount to ensuring the safety and reliability of connected devices and the data they exchange. By incorporating robust security practices into the API development lifecycle, developers can mitigate vulnerabilities and protect sensitive information.
Essential Security Considerations for Developing Secure IoT APIs
Developing secure APIs for IoT requires a comprehensive approach, encompassing various security considerations. Here’s a list of essential factors to incorporate:
- Authentication and Authorization: Implement strong authentication mechanisms to verify the identity of API clients and ensure only authorized entities can access sensitive data. Employ robust authentication protocols such as OAuth 2.0 or OpenID Connect.
- Data Encryption: Encrypt sensitive data both in transit and at rest using industry-standard encryption algorithms. This prevents unauthorized access to confidential information, such as device credentials, user data, and sensor readings.
- Input Validation and Sanitization: Thoroughly validate and sanitize all API inputs to prevent injection attacks, such as SQL injection or cross-site scripting (XSS). This practice helps ensure the integrity of data and prevents malicious code execution.
- Rate Limiting: Implement rate limiting mechanisms to prevent denial-of-service (DoS) attacks by limiting the number of API requests a client can make within a specific timeframe. This safeguards the API from excessive traffic and ensures its availability for legitimate users.
- Secure Communication Protocols: Utilize secure communication protocols such as HTTPS (TLS/SSL) to encrypt data exchanged between API clients and servers. This protects data from eavesdropping and tampering during transmission.
- API Versioning: Implement API versioning to facilitate updates and security enhancements without disrupting existing clients. This allows developers to address vulnerabilities and introduce new features while maintaining compatibility with older versions.
- Security Auditing: Regularly conduct security audits to identify potential vulnerabilities and ensure compliance with industry best practices. This proactive approach helps uncover weaknesses before they can be exploited by malicious actors.
Best Practices for Code Review, Vulnerability Scanning, and Secure Coding Techniques
Code review, vulnerability scanning, and secure coding techniques are crucial for building robust and secure IoT APIs.
- Code Review: Implement a rigorous code review process involving multiple developers with different expertise. This helps identify potential security flaws and coding errors before deployment. Static analysis tools can be used to automate the code review process and identify common vulnerabilities.
- Vulnerability Scanning: Regularly scan the API codebase using automated vulnerability scanners to identify potential security weaknesses. These tools can detect common vulnerabilities such as SQL injection, cross-site scripting, and buffer overflows.
- Secure Coding Practices: Adhere to secure coding practices, such as avoiding insecure functions, using secure libraries, and properly handling exceptions. This helps minimize the risk of introducing vulnerabilities during development.
- Threat Modeling: Conduct threat modeling exercises to identify potential threats and vulnerabilities that could impact the API. This helps prioritize security efforts and allocate resources effectively.
Incorporating Security Features into the API Development Lifecycle
Integrating security features into the API development lifecycle is essential for building secure IoT APIs.
You also can investigate more thoroughly about The Best Cloud Storage and File-Sharing Services to enhance your awareness in the field of The Best Cloud Storage and File-Sharing Services.
- Security by Design: Integrate security considerations from the initial design phase of the API. This ensures that security is built into the foundation of the API, rather than being an afterthought.
- Security Testing: Conduct thorough security testing throughout the development lifecycle, including penetration testing, fuzzing, and security audits. This helps identify and mitigate vulnerabilities before deployment.
- Continuous Monitoring: Monitor the API for suspicious activity and security breaches. Implement intrusion detection and prevention systems to detect and respond to attacks in real-time.
Secure API Management for IoT: The Ultimate Guide To API Security For IoT
In the vast and interconnected landscape of the Internet of Things (IoT), where devices communicate and exchange data seamlessly, securing the APIs that power these interactions is paramount. API gateways and management platforms play a pivotal role in safeguarding IoT APIs from various threats, ensuring data integrity, and maintaining the reliability of connected systems.
API Gateways and Management Platforms
API gateways act as a central point of control and security for all API traffic in an IoT ecosystem. They provide a layer of abstraction between client applications and backend services, enabling centralized management, security enforcement, and monitoring of API interactions.Management platforms, on the other hand, offer comprehensive tools for managing, monitoring, and securing APIs throughout their lifecycle.
These platforms empower developers and security teams to define policies, enforce access controls, monitor API usage, and respond to security incidents effectively.
Implementing Rate Limiting, Throttling, and Access Control
To mitigate the risk of API abuse and protect resources from overwhelming demands, implementing rate limiting and throttling mechanisms is crucial. Rate limiting sets limits on the number of requests that can be made within a specific time frame, preventing malicious actors from flooding APIs with excessive traffic.
Throttling, on the other hand, dynamically adjusts the rate of requests based on real-time usage patterns, ensuring a smooth and responsive API experience for legitimate users.Access control mechanisms are essential for enforcing granular permissions and restricting access to sensitive data.
Implementing role-based access control (RBAC) allows administrators to define different roles for users or devices, granting them access to specific resources based on their assigned permissions.
Monitoring API Traffic and Detecting Security Incidents
Effective monitoring of API traffic is essential for identifying and responding to potential security incidents. API management platforms offer comprehensive monitoring capabilities, providing insights into API usage patterns, response times, and error rates. Anomaly detection algorithms can analyze traffic patterns and flag suspicious activities, such as sudden spikes in requests, unusual access patterns, or attempts to exploit vulnerabilities.
- Real-time Monitoring:Continuous monitoring of API traffic provides valuable insights into usage patterns, potential anomalies, and security threats. This allows for prompt detection and mitigation of incidents.
- Log Analysis:Thorough analysis of API logs helps identify suspicious activities, such as unauthorized access attempts, data breaches, or attempts to exploit vulnerabilities.
- Alerting and Notifications:Configuring alerts for critical events, such as unauthorized access, API failures, or suspicious traffic patterns, enables timely responses to security incidents.
Securing Data Transmission and Storage

The security of data transmission and storage is paramount in IoT systems. Sensitive data, such as user information, sensor readings, and control commands, must be protected from unauthorized access, interception, and manipulation. Secure data transmission protocols and robust storage mechanisms are essential to maintain the integrity and confidentiality of IoT data.
Secure Data Transmission Protocols
Secure data transmission protocols are crucial for protecting data during transit between IoT devices, gateways, and cloud platforms. These protocols ensure data confidentiality, integrity, and authentication, preventing eavesdropping, data tampering, and unauthorized access.
- Transport Layer Security (TLS) and Secure Sockets Layer (SSL):TLS and SSL are widely used protocols for establishing secure communication channels over the internet. They use encryption to protect data from eavesdropping and ensure data integrity through digital signatures. TLS is the successor to SSL and offers enhanced security features.
- Message Queuing Telemetry Transport (MQTT):MQTT is a lightweight messaging protocol designed for constrained devices. It supports TLS for secure communication and offers features like authentication and access control. MQTT is particularly suitable for IoT applications where resource constraints are a major concern.
- Data-at-Rest Encryption:Encrypting data while it is stored on devices, gateways, or cloud servers protects it from unauthorized access even if the storage system is compromised. Encryption algorithms like Advanced Encryption Standard (AES) are commonly used for data-at-rest encryption.
Encryption Methods for IoT Data
Different encryption methods offer varying levels of security and performance characteristics, making it essential to choose the appropriate method based on the specific requirements of the IoT application.
- Symmetric Encryption:Symmetric encryption uses the same key for both encryption and decryption. This method is generally faster than asymmetric encryption but requires secure key distribution. Examples include AES and Blowfish.
- Asymmetric Encryption:Asymmetric encryption uses separate keys for encryption and decryption. This method is more secure than symmetric encryption as it does not require the distribution of the private key. However, it is computationally more demanding. Examples include RSA and ECC.
- Homomorphic Encryption:Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. This method is particularly useful for privacy-preserving data analysis in IoT applications. However, it is computationally expensive and currently not widely used in practice.
Best Practices for Securing Data Storage
Secure data storage is essential to protect sensitive IoT data from unauthorized access, modification, or deletion.
- Data Minimization:Only collect and store the data that is absolutely necessary for the intended purpose of the IoT application. This minimizes the potential impact of a data breach.
- Access Control:Implement robust access control mechanisms to restrict access to sensitive data based on user roles and permissions. This prevents unauthorized access and ensures data integrity.
- Data Backup and Recovery:Regularly back up IoT data to ensure its availability in case of data loss or system failures. Implement disaster recovery plans to restore data and services quickly and efficiently.
- Regular Security Audits:Conduct regular security audits to identify vulnerabilities and ensure that data storage practices comply with security standards and best practices.
Implementing Secure Authentication and Authorization
Secure authentication and authorization are crucial components of API security for IoT. They ensure that only authorized devices and users can access sensitive data and resources. Authentication verifies the identity of the requestor, while authorization determines what actions the requestor is allowed to perform.
Authentication Mechanisms for IoT APIs
Authentication mechanisms play a vital role in verifying the identity of devices and users attempting to access IoT APIs. They ensure that only legitimate entities can interact with the system, preventing unauthorized access and data breaches.
- OAuth 2.0: This widely adopted standard allows devices and users to grant limited access to their resources without sharing their credentials. It uses access tokens to authorize requests, enhancing security and flexibility.
- JSON Web Token (JWT): A compact and self-contained way to securely transmit information between parties as a JSON object. It includes a payload containing user information and is signed using a secret key, ensuring its authenticity and integrity.
- API Keys: Simple yet effective for identifying clients. API keys are unique identifiers assigned to each device or user, allowing for easy tracking and management of access.
- Mutual TLS (mTLS): This robust mechanism involves both the client and server exchanging digital certificates for authentication. It ensures secure communication and verifies the identity of both parties involved in the transaction.
Authorization Rules for Restricting Access
Authorization rules define the specific actions that authenticated devices and users are permitted to perform. These rules are essential for implementing fine-grained access control and ensuring that sensitive data is protected.
- Role-Based Access Control (RBAC): This approach assigns roles to users and devices, granting them specific permissions based on their assigned roles. For instance, a “sensor” device might only have read access to sensor data, while an “administrator” user might have full access to all resources.
- Attribute-Based Access Control (ABAC): This more flexible approach allows for granular control based on specific attributes of the user, device, or context. For example, a rule might allow access to a specific API endpoint only if the device is located within a specific geographic region.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This makes it significantly harder for unauthorized individuals to gain access, even if they have obtained one of the authentication factors.
- Knowledge Factor: Something the user knows, such as a password or PIN.
- Possession Factor: Something the user has, such as a smartphone or security token.
- Inherence Factor: Something the user is, such as a fingerprint or facial scan.
Vulnerability Management and Patching
In the dynamic landscape of IoT, ensuring the security of your API is a continuous process that requires proactive vulnerability management and patching. This involves identifying potential weaknesses in your API, mitigating them before they can be exploited, and keeping your systems updated with the latest security patches.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are crucial for identifying vulnerabilities in IoT systems. These assessments provide an objective evaluation of your security posture, uncovering potential weaknesses that might be missed during development or deployment.
- Security Audits: Security audits involve a systematic examination of your API and its supporting infrastructure to identify potential security vulnerabilities. These audits typically involve a comprehensive review of your API code, configuration files, and network infrastructure, using industry-standard security tools and methodologies.
- Penetration Testing: Penetration testing simulates real-world attacks on your API, attempting to exploit vulnerabilities and gain unauthorized access to your system. These tests are conducted by ethical hackers who use a variety of techniques to assess the strength of your security controls and identify potential weaknesses.
Strategies for Patching and Updating IoT Devices and APIs
Maintaining the security of your IoT systems requires a robust patching and updating strategy. This involves promptly addressing vulnerabilities as they are discovered and ensuring that all devices and APIs are running the latest security patches.
- Automated Patching: Implementing automated patching mechanisms can streamline the process of updating your IoT devices and APIs. This involves configuring your systems to automatically download and install security patches as they become available, minimizing the risk of vulnerabilities being exploited.
- Regular Updates: It’s crucial to establish a regular schedule for updating your IoT devices and APIs. This should involve regularly checking for new security patches and promptly applying them to all devices and APIs in your ecosystem.
- Version Control: Implement version control for your API code, enabling you to track changes and roll back to previous versions if a patch introduces unexpected issues. This provides a safety net and ensures that you can revert to a known working state if necessary.
Secure API Integration with IoT Devices
Integrating APIs with IoT devices presents unique challenges due to the heterogeneity of devices, their limited processing power and connectivity, and the need to ensure secure data exchange. This section delves into the key considerations and best practices for establishing secure API integrations in IoT environments.
Secure Communication Protocols for Device-to-API Interactions
Selecting a secure communication protocol is crucial for protecting data exchanged between IoT devices and APIs. The protocol should provide confidentiality, integrity, and authentication to prevent unauthorized access and data tampering.
- MQTT (Message Queuing Telemetry Transport):A lightweight messaging protocol commonly used in IoT for real-time communication. MQTT supports secure communication over TLS/SSL, ensuring data confidentiality and integrity.
- CoAP (Constrained Application Protocol):A protocol designed for resource-constrained devices, optimized for low-bandwidth and high-latency networks. CoAP supports DTLS (Datagram Transport Layer Security) for secure communication.
- HTTP/2:The latest version of the Hypertext Transfer Protocol offers enhanced performance and security features, including TLS/SSL encryption and HTTP/2 Server Push for efficient data delivery.
Securing Device Authentication and Data Exchange
Device authentication is critical for verifying the identity of IoT devices connecting to APIs. This helps prevent unauthorized access and data manipulation.
- Mutual TLS (Transport Layer Security):A robust authentication mechanism where both the device and the API server present certificates to verify their identities. Mutual TLS ensures secure communication and protects against man-in-the-middle attacks.
- Digital Signatures:Devices can use digital signatures to verify the authenticity and integrity of data sent to APIs. Digital signatures use cryptographic algorithms to create a unique code that can be verified by the API server.
- API Keys:API keys are unique identifiers that can be used to authenticate devices and control access to specific API resources. API keys should be generated and managed securely to prevent unauthorized use.
Future Trends in IoT API Security
The rapidly evolving IoT landscape, characterized by interconnected devices and vast data flows, presents unique challenges for API security. As the number of connected devices and the complexity of IoT ecosystems continue to grow, so too do the threats targeting these systems.
Understanding and adapting to emerging trends in IoT API security is crucial for safeguarding data, protecting privacy, and ensuring the resilience of IoT applications.
Emerging Security Threats and Vulnerabilities
The expanding attack surface of the IoT ecosystem introduces new security threats and vulnerabilities. Here are some key trends:
- Rise of sophisticated attacks:Advanced attackers are leveraging sophisticated techniques, including zero-day exploits, botnets, and distributed denial-of-service (DDoS) attacks, to target IoT APIs. These attacks often exploit vulnerabilities in device firmware, API endpoints, and communication protocols, aiming to compromise sensitive data, disrupt operations, or gain unauthorized access.
- Exploitation of edge computing vulnerabilities:The proliferation of edge computing in IoT environments creates new security challenges. Edge devices, with their limited processing power and security resources, are susceptible to attacks that exploit vulnerabilities in their software and hardware. These attacks can compromise data stored on edge devices, disrupt device functionality, or even enable malicious actors to control them.
- Increasing use of machine learning (ML) in attacks:Attackers are increasingly using ML techniques to automate and refine their attacks, making them more difficult to detect and mitigate. ML algorithms can be used to identify and exploit vulnerabilities, generate realistic phishing emails, and evade security controls.
- Privacy concerns and data breaches:IoT devices collect vast amounts of personal data, raising concerns about privacy and data security. Breaches involving IoT devices can expose sensitive information, including location data, health records, and financial details, leading to identity theft, financial fraud, and other serious consequences.
Role of Blockchain, AI, and Cryptography
Emerging technologies, such as blockchain, AI, and cryptography, offer promising solutions for enhancing IoT API security.
- Blockchain for secure data management:Blockchain technology can enhance data integrity and security in IoT systems by providing a tamper-proof, decentralized ledger for recording transactions and data exchange. This can help prevent data manipulation, ensure provenance, and enhance trust in IoT data.
- AI for threat detection and prevention:AI-powered security solutions can analyze large volumes of data from IoT devices and networks to identify patterns and anomalies that indicate potential attacks. These solutions can learn from past attacks and adapt to new threats, providing real-time threat detection and prevention.
- Cryptography for secure communication and data protection:Strong cryptography is essential for securing communication between IoT devices and APIs, as well as protecting data at rest and in transit. Advanced encryption algorithms, digital signatures, and secure authentication protocols can help prevent unauthorized access, data interception, and tampering.
Future of API Security Standards and Regulations
The evolving threat landscape and increasing reliance on IoT APIs necessitate the development of robust security standards and regulations.
- Standardized API security frameworks:The development of standardized API security frameworks, such as the Open Web Application Security Project (OWASP) API Security Top 10, can provide a common set of guidelines and best practices for secure API development and deployment. These frameworks can help organizations identify and address common vulnerabilities, improve security posture, and ensure compliance with industry standards.
- Industry-specific regulations:As the use of IoT devices expands across different sectors, industry-specific regulations are emerging to address security concerns and ensure responsible data management. For example, the healthcare industry has implemented regulations like HIPAA to protect patient data, while the automotive industry is developing standards for connected vehicles.
- Government initiatives:Governments worldwide are recognizing the importance of IoT security and are enacting legislation and implementing initiatives to promote secure IoT development and deployment. These initiatives often focus on areas such as data privacy, cybersecurity, and the development of secure standards and certifications.
Last Recap
In the dynamic world of the IoT, where innovation and connectivity are paramount, API security is no longer a luxury but a necessity. By embracing the principles Artikeld in this guide, organizations can mitigate the risks associated with API vulnerabilities, safeguard their valuable data, and ensure the continued growth and prosperity of the IoT ecosystem.
As the IoT continues to evolve, the need for a comprehensive and proactive approach to API security will only become more critical. This guide provides a solid foundation for building a secure and resilient IoT infrastructure, enabling businesses to harness the transformative power of connected devices with confidence.
Helpful Answers
What are some common API security threats in the IoT?
Common threats include unauthorized access, data manipulation, denial-of-service attacks, and injection vulnerabilities. These attacks can compromise the integrity of IoT devices, steal sensitive data, and disrupt critical operations.
How can I implement secure authentication and authorization for IoT APIs?
Implement robust authentication mechanisms like OAuth 2.0 and JSON Web Tokens (JWT) to verify user identities. Establish authorization rules to control access to specific API resources based on user roles and permissions. Consider multi-factor authentication (MFA) for an extra layer of security.
What are some emerging trends in IoT API security?
Emerging trends include the use of blockchain technology for secure data sharing, AI-powered threat detection and response, and the development of new cryptographic algorithms to enhance data protection. These advancements will play a crucial role in shaping the future of IoT API security.